Most malware that is delivered as an email attachment is usually a Word (.docx) or Excel (.xlsx) file. Cybersecurity threat analysts have recently discovered that PDF attachments are now becoming more popular to distribute malware. Since many people have been trained to be suspicious of opening Word and Excel files, they are not as cautious about opening a PDF. But there’s a twist, the malware inside the PDF is still Word document.
This is how the PDF tricks the user who receives one of these phishing emails into loading the malware lurking inside.
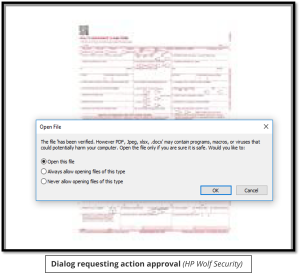
Sources: Bleeping Computer, HP Wolf Security
May 24, 2022

Total Medical Compliance
6124 Creft Circle
Indian Trail, NC 28079
Phone: (888) 862-6742
Fax: (866) 875-3809
©2023 Total Medical Compliance

Total Medical Compliance
6124 Creft Circle
Indian Trail, NC 28079
(888) 862-6742
Fax (866) 875-3809
©2022 Total Medical Compliance